EKS Authentication - Summary
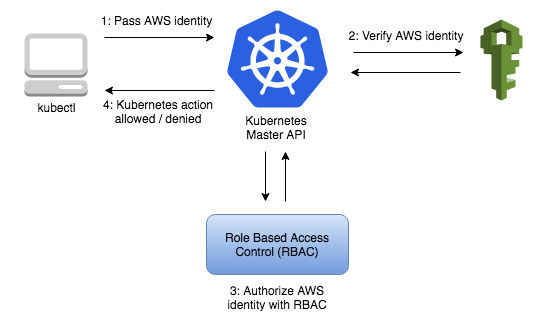
Amazon EKS uses IAM to provide authentication to your Kubernetes cluster.
It uses aws eks get-token command, available in version 1.16.156 or greater of the AWS CLI, or the AWS IAM Authenticator for Kubernetes
And for authorization, it still relies on native Kubernetes Role Based Access Control (RBAC)
- When you create an Amazon EKS cluster, the IAM entity user or role (for example, for federated users) that creates the cluster is automatically granted system:masters permissions in the cluster’s RBAC configuration
Here are the steps for adding additional users to the EKS Cluster
- Create IAM Policy
- Create IAM User and attach the Policy
- Update EKS aws-auth configmap
- Create EKS Cluster Role
- Create EKS Cluster Role Binding
- Create IAM Access Key Pair
- Configure Kubectl
- Generate kubeconfig
EKS Read-Only User
1. Create IAM Policy for EKS Read-Only Access
CLI
1
aws iam create-policy --policy-name=eks-readonly-policy --policy-document='{"Version": "2012-10-17", "Statement": {"Sid": "45345354354", "Effect": "Allow", "Action": ["eks:DescribeCluster", "eks:ListCluster" ], "Resource": "*" }}'
Console
1
2
3
4
5
6
7
8
9
10
11
12
{
"Version": "2012-10-17",
"Statement": {
"Sid": "45345354354",
"Effect": "Allow",
"Action": [
"eks:DescribeCluster",
"eks:ListCluster"
],
"Resource": "*"
}
}
2. Create IAM User and attach EKS Read-Only Policy
CLI
1
2
3
aws iam create-user --user-name=eks-readonly-user
aws iam attach-user-policy --user-name=eks-readonly-user --policy-arn=arn:aws:iam::xxxxxxxx:policy/eks-readonly-policy
Console
IAM > User > Add User
3. Update EKS aws-auth configmap
Dump existing configmap
1
kubectl -n kube-system get configmap aws-auth -o yaml > aws-auth.yaml
Edit aws-auth.yaml and add additional users to mapUsers secion. You will need to provide the IAM User ARN and an Username to be used in Kubernetes. Better to use same username to avoid confusion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
apiVersion: v1
kind: ConfigMap
metadata:
name: aws-auth
namespace: kube-system
data:
mapRoles: |
- rolearn: arn:aws:iam::xxxxxxxxxxxxx:role/XXXXXXXXXX-STA-NodeInstanceRole-XXXXXX
username: system:node:
groups:
- system:bootstrappers
- system:nodes
mapUsers: |
- userarn: arn:aws:iam::xxxxxxxxxxxxx:user/eks-readonly-user
username: eks-readonly-user
Apply aws-auth configmap
1
kubectl apply -f aws-auth.yaml
4. Create an EKS ClusterRole
Create file eks-readonly-user-role.yaml with following snippet and apply using kubectl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: eks-readonly-user-role
rules:
- apiGroups:
- ""
resources:
- '*'
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- '*'
verbs:
- get
- list
- watch
- apiGroups:
- apps
resources:
- '*'
verbs:
- get
- list
- watch
1
kubectl apply -f eks-readonly-user-role.yaml
5. Create an EKS ClusterRoleBinding
Create file eks-readonly-user-role-binding.yaml with following snippet and apply using kubectl
1
2
3
4
5
6
7
8
9
10
11
12
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: eks-readonly-user-role-binding
subjects:
- kind: User
name: eks-readonly-user
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: eks-readonly-user-role
apiGroup: rbac.authorization.k8s.io
1
kubectl apply -f eks-readonly-user-role-binding.yaml
Next steps are to be performed in User's console
6. Create IAM Access Key Pair
CLI
1
aws iam create-access-key --user-name eks-readonly-user
Console
IAM > User > Security Credentials > Create access key
7. Configure kubectl
Ref https://dijeesh.github.io/Setting-up-kubectl-for-EKS and setup kubectl for your local environment.
8 Generate kubeconfig
1
aws eks --region xx-xxx-x update-kubeconfig --name xxx-eks-cluster
Replace region and cluster name.
Done, Try runnig kubectl commands and you should be now have readonly access to the EKS Cluster.
References
Research Partner : Sahir Abbas
